Maximum IT security
The multi-layered security concept
Your contact person
IT Security Protection
IT outsourcing and IT security – The multi-level IT security concept from noris network
Especially in times of data theft, the importance of information security is often underestimated. Securing sensitive data and important business processes is a critical success factor for the competitiveness of companies. You can meet these challenges with a good feeling if you have a competent partner who takes care of the security of your IT.
The possible risks for your IT security are manifold: from cyber attacks to DDoS attacks, phishing through intrusion, theft or sabotage. This requires that your defense mechanisms are equally complex. We promise you safety and quality at the highest level and prove this with our numerous certifications.
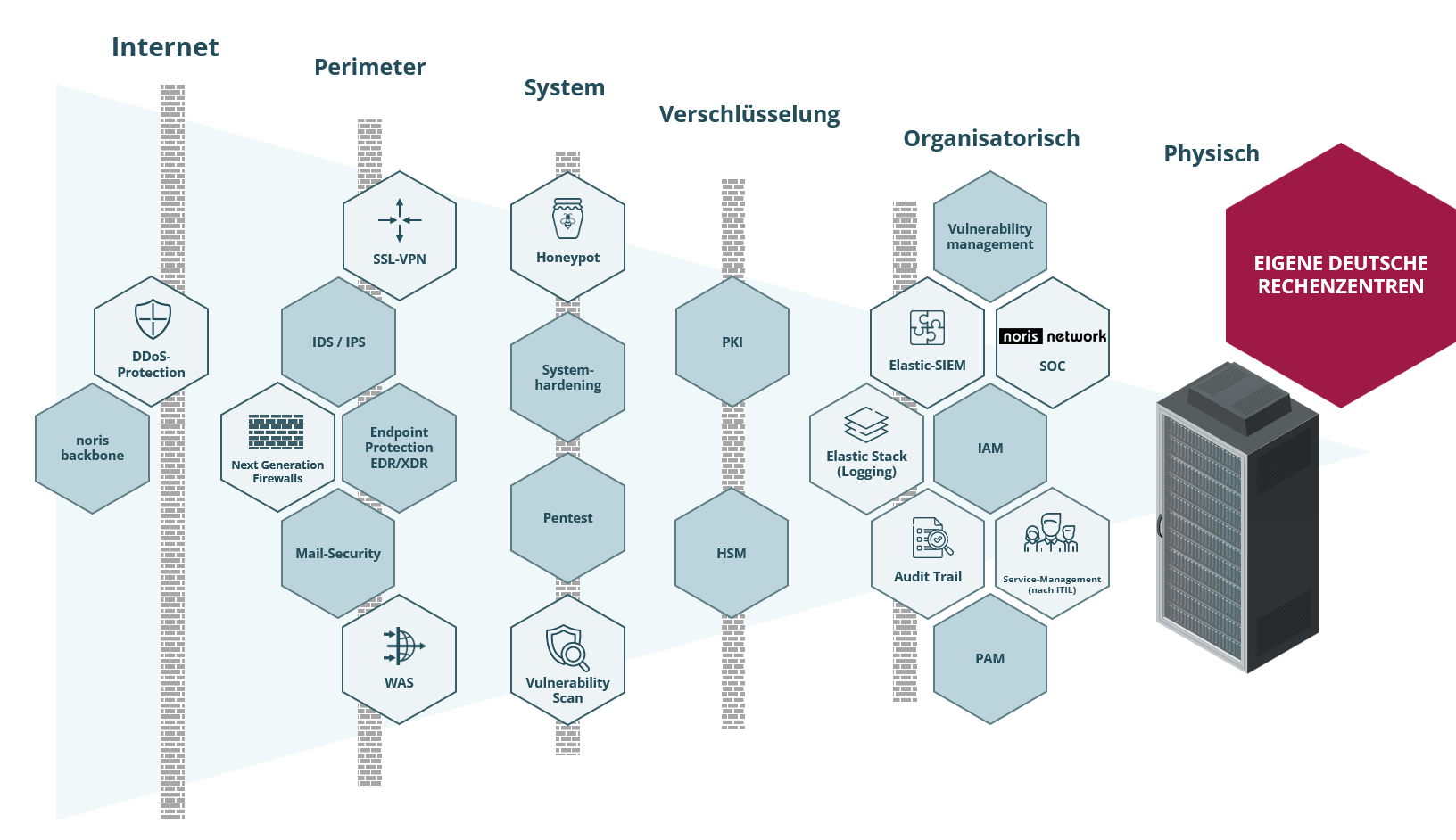
We have set up a multi-layered, comprehensive IT security barrier – to ensure maximum protection of your systems!
Your advantages:
- Active protection for against internal and external threats
- Central security management for your entire setup
- Detection of security threats and their elimination Security Incidents
- Fulfillment of obligations for KRITIS operators (e.g. compliance with the IT Security Act 2.0)
- Reduction of security and liability risks
- Transparency through regular reporting
Botnet Interception
Botnet Interception is an early warning system for detecting attacks. Blacklists of command-and-control servers are generated in real time. Botnets within the customer’s infrastructure are thus detected and Advanced Persistent Threats can be combated.
noris network Backbone
With our own backbone there is no danger of network overload. Not even in the case of massive DDoS attacks.
DDoS Protection
Thanks to noris network’s comprehensive DDoS protection, DDoS attacks on customer systems can be mitigated so that they remain available even during a massive attack. Harmful traffic is already filtered at nodes in the company’s own backbone by means of ACLs.
Vulnerability Scan
The Vulnerability Scan checks the components of your systems internally and externally for vulnerabilities. Detailed reports provide recommendations on how to proactively fix the vulnerabilities. Vulnerability Scans thus detect vulnerabilities in your IT systems before
SSL-VPN
SSL VPN can be used to establish secure access to the systems in the noris network data centers and, if necessary, to combine this with two-factor authentication. Your employees can thus easily connect mobile devices, home offices and offices securely via the Internet. The security of your systems is guaranteed, as they are not located directly on the Internet, but behind the SSL VPN gateway.
Next Generation Firewalls
Next Generation Firewalls are firewalls that not only serve as packet filters and open or close ports, but also filter traffic at the application level and enable effective DLP (Data Leakage Prevention). All systems are hosted in our data centers. This means that your systems are optimally connected to the Internet and protected from unauthorized access.
Web Application Security Service (WAS)
Especially when sensitive data is processed in your web application, a high level of protection is important. With the Web Application Security Service from noris based on a high-end Web Application Firewall (WAF), we offer you comprehensive protection for your web applications. For fault-tolerant operation, the Web Application Firewall and the optional load balancer are operated in active-passive clusters.
Intrusion Detection (IDS) / Intrusion Prevention (IPS)
With IDS systems the data traffic of your systems is monitored and detected, e.g. exploit attempts are alerted in real time. With IPS systems, the protection goes even further, as they immediately prevent the attack by for example dropping packets or closing sessions.
Honeypot
With a honeypot, attackers are lured in and deceived by simulated IT systems. For better analysis, honeypots have an extended logging function, so they usually log every input and, if necessary, also store the attacker’s payload. Attack patterns are thus recognized and countermeasures can be initiated more quickly to provide additional external protection for productive systems.
Endpoint Protection
Even complex threats are identified by adaptive security and optimized by additional program, web and device controls. Endpoint protection is used to prevent unwanted data leakage and thus protect against data breaches.
Identity and Access Management (IAM)
IAM is used to centrally manage access rights to systems and applications. This ensures processes so that it is always clear who needs and receives certain rights on which system.
Privileged Access Management (PAM)
With PAM, access rights for administrators and other privileged users are defined and limited to what is necessary for operation. This protects your infrastructure from unauthorized and unauthorized access from the inside.
Elastic Stack
The Elastic Stack is an open source product and consists of Elastic Search, Logstash and Kibana. It enables extensive and powerful search, correlation of log data, graphical analysis and monitoring in real time. Thus, attacks can be identified across system boundaries. This allows you to react quickly to system events or facilitate your auditing.
Security Operations Center (SOC)
Consists of a team of IT security experts that monitors the messages from your IT security systems (e.g. Honeypot, IAM, PAM and SIEM etc.) Security threats are proactively identified and remediation actions are initiated. The SOC has a complete overview of the security events of all submitting systems.
Security Information and Event Management (SIEM)
SIEM is used to collect security-relevant information and data from your systems. Automated alerting enables timely responses to security incidents. This provides you with indications of threatening attacks and preventive measures in the security context of your environment.
Service management according to ITIL
The certified service managers at noris provide you and your systems with comprehensive support and keep an eye on all service processes. This enables full cost and performance transparency.
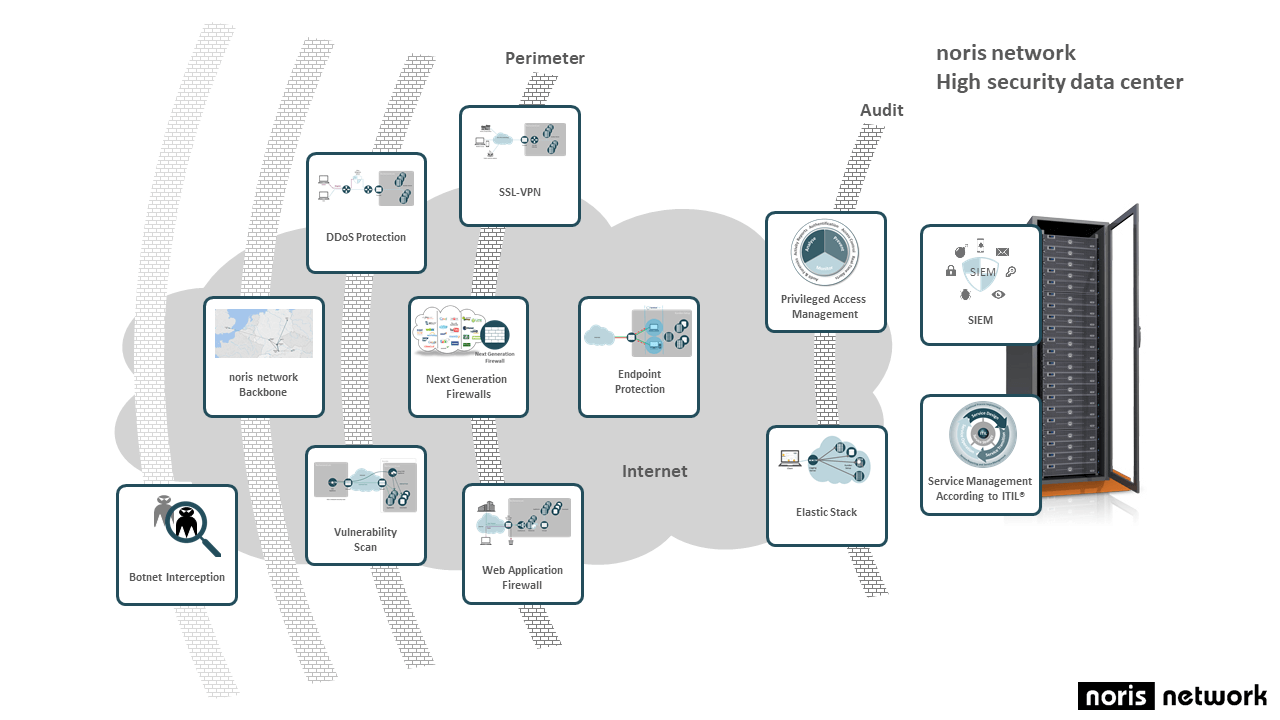
DDoS protection: The comprehensive DDoS protection mechanisms deployed by noris network allow to mitigate DDoS attacks to customer systems and thus ensure that these systems remain available even while subjected to a massive attack.
SSL VPN: SSL VPNs allow to provide secure access to the systems operating in noris network’s data centers and can optionally be combined with two-factor authentication.
noris network backbone: By supporting up to 4 Tbps of bandwidth, the backbone eliminates the risk of overloading the network. Not even in the event of massive DDoS attacks.
Next-generation firewalls: Next-generation firewalls are firewall mechanisms which not only serve as packet filters and open or close ports, but also filter the traffic on the application layer and support an effective DLP (Data Leakage Prevention).
Endpoint Protection: Even complex threats are identified through adaptive security and optimized through additional program, web and device controls.
Privileged Access Management: Network Security aplliance acts like a flight recorder and is used to guarantee the exact logging and tracking of all access to the systems. This ensures that no anonymous users can make changes to a system. Access to the data stored in the Shell Control Box is exclusively granted in accordance with the four eyes principle. This makes it easily possible to also audit administrators and thereby protect them against internal attacks.
SIEM: Security Information and Event Management (SIEM) is the central approach to collect, evaluate and report security-related information and provides compliance reports about all security events. Warnings enable prompt reactions to security incidents. SIEM also offers the management of security-relevant data and analyses. This makes it possible to search for events in the past to support IT forensic investigations.
Botnet interception: Botnet interception is an early warning mechanism that detects attacks. Blacklists identifying command-and-control (C&C) servers are generated in real time. This allows to detect botnets existing within the customer’s infrastructure and thus counter advanced persistent threats.
Security check: The security check evaluates the components of the customer systems internally and externally for the presence of weak points. Detailed reports provide recommendations on how such vulnerabilities can be removed proactively.
WAF: Web applications can be provided with double protection by setting up a web application firewall (in addition to a traditional firewall) to successfully ward off attacks such as cross-site scripting or SQL injection.
Elastic Stack: The Elastic Stack is an open-source product consisting of Elastic Search, Logstash, and Kibana. It supports comprehensive and powerful search functions, correlation of log data, graphical evaluations, and real-time monitoring. This allows to identify attacks across system boundaries.
Service management according to ITIL®: noris network’s service managers serve our customers and their systems in a holistic manner and always keep an eye on all service processes. This creates full cost and performance transparency.